Today’s computers are governed by the laws of classical physics and Moore’s law2 which states that, historically speaking, computers double their speed and capacity every 18 months because chip makers are able to squeeze twice as many transistors onto a computer chip.
In order for these computing improvements to continue, placing more transistors on a computer chip means that transistors need to get smaller. But physics presents a natural barrier in that once technology has shrunk a transistor to the size of a single atom there are no more improvements to be made to transistor size. But what if the transistor could be replaced with a better technology, a technology that allows for a new paradigm of computing?
The laws of physics that can be seen, observed, and understood through experiences in everyday life are referred to as classical physics, and these laws govern the workings and computational capabilities of computers as they are known today. Quantum computers, obeying the laws of quantum mechanics, can calculate things in ways that are unimaginable from the perspective of people’s regular day-to-day experiences.
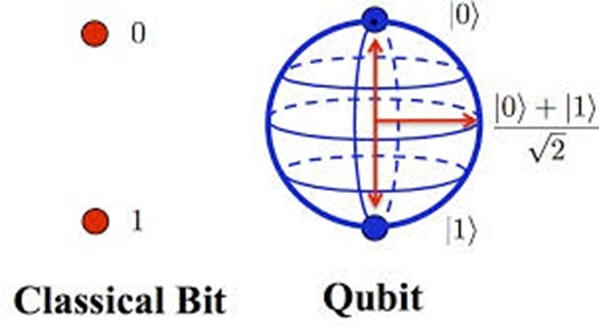
Quantum mechanics has some novel properties that researchers have realized can be harnessed to make quantum computers that behave very differently than the classical computers commonly used today. Using these novel quantum properties, a quantum computer is able to solve certain problems like searching and factoring much faster than the time it would take a classical computer, with the best known algorithms, to solve the same problem.
In practice, there are a number of physical systems that realize different implementations of quantum computers. Some common systems are nuclear spins, superconducting qubits, ion traps, and optical cavity quantum electrodynamics. Each research direction is at a different level of maturity, with some being stronger contenders than others for large-scale quantum computing.
How does quantum computing impact cryptography and security?
Cryptography plays a very important role in most secure electronic communication systems today because it ensures that only authentic parties can read each other’s exchanged messages.A quantum computer cannot break all types of cryptographic keys and some cryptographic algorithms in use today are also safe to use in a world of widespread quantum computing.
What does quantum-safe mean?
Security controls that are known to be highly vulnerable to quantum attack, and can be easily broken by a quantum computer, include:
- Any cryptosystem that is built on top of the mathematical complexities of Integer Factoring and
Discrete Logarithms. This includes RSA, DSA, DH, ECDH, ECDSA and other variants of these
ciphers. It is important to point out that almost all public key cryptography in fielded security
products and protocols today use these types of ciphers. - Any security protocols that derive security from the above public key ciphers.
- Any products or security systems that derive security from the above protocols.